3. Transparency - Flock
Flock says that they believe in transparency, but do they meaningfully practice it?
The first red flag is that Flock's website is blocked on the Wayback Machine. The Wayback Machine is an internet archive that takes snapshots of webpages
at different times, allowing people to see old versions of webpages in case anything changes. When eyesoffgsp.org quotes Flock's blog to demonstrate their attitude towards something,
Flock could later edit the blog and there won't be a good way to prove what they originally said. In contrast, the eyesoffgsp.org code is stored on GitHub,
meaning anyone can see every change that was ever made to the website.
Speaking of Flock's blog, they posted a three part series on transparency. Here's how they introduce the series:
If they're trying to say that they want to make transparency easier so that officers can spend more time fighting crime and less time on FOIA requests, this is the worst way to say it. The connotations imply a loathing of transparency and a hint of disregard for the rule of law and constitutional protections. But there's still two more posts, so let's see if they double down or redeem themselves:
If they're trying to say that there used to not be an easy way to redact confidential info, this is the worst way to say it. It feels like coded language for an intent
to make it easier for agencies to disclose as little information as possible in FOIA requests, when considering the context of how the search reason field has been used in the past, with thousands of examples of
"investigation," "suspect," "donut," "asdf," and similarly vague or meaningless terms being revealed through FOIA requests.[8][9]
In order to address those concerns, Flock went on to introduce a new feature: mandatory Offense Type drop-down selection. Now, if an officer is
stalking his ex-girlfriend, instead of typing "inves" as the search reason, he will just have to pick a random crime from the drop-down to pretend to
be investigating. This does little to help leadership monitor use of the system, but let's look at a solution that could.
An independent analyst used sample data to build a search anomaly dashboard (below).[10]
It graphs a user's historical search queries by hour and performs statistical analysis to flag suspicious search frequencies or other anomalies.
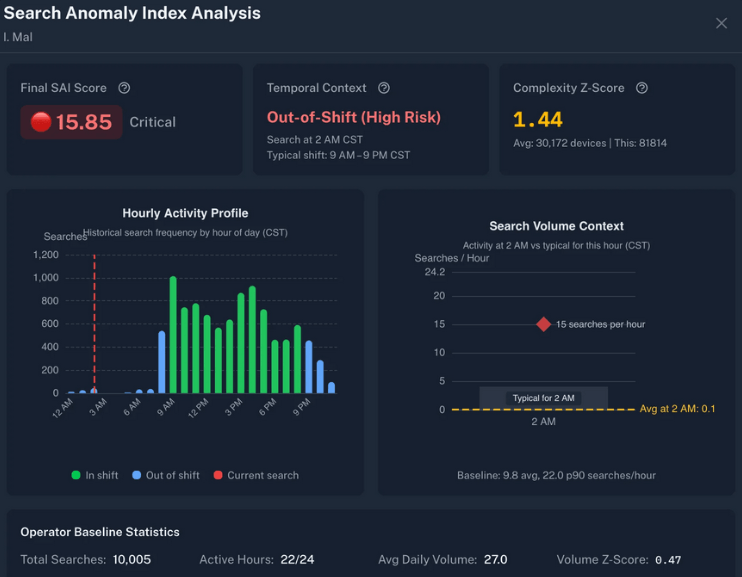
Building on this example dashboard, the system could then have automated alerts, or weekly user analytics reports sent to supervisors for review.
It's not a very big ask for a multi-billion dollar company to think of or to implement something that an independent analyst can put together in their free time.
Flock could have developed analytics and reporting features years ago, but instead they've been developing new products (something that actually generates revenue).
It's also worth noting that law enforcement and council leaderships have not been demanding such accountability measures as customers.
It's easy to talk about transparency, but true values are imbued into all actions big and small, from decision-making to simple word choices. Flock has demonstrated
that they are unable or unwilling to put transparency first.
Update 12/17/25: Flock tried to shut down the website of the independent analyst mentioned here, by falsely accusing them of phishing and trademark infringement.[11]
Update 12/19/25: 404 Media reported back in May 2025 that Flock's upcoming product Nova uses breached data obtained from the dark web based on leaked information.[12]
This would mean that officers could perform a person search in Nova and receive information about them that was leaked in a data breach. Flock tried to gaslight everyone by explaining that
the dark web data discussions only surfaced because some of the agencies in the beta program asked for the option but ultimately they decided not to pursue it.[13]
However, an independent researcher uncovered evidence that says otherwise.[14] By inspecting the html code of the Nova front-end website, the
researcher showcases data sources explicitly named "Dark Data" with fields for social security number, credit card number, IP addresses, and other sensitive types of personal information.